Google Workspace SAML setup #
Starburst Galaxy supports configuring Google Workspace as a single sign-on identity provider. Google Workspace was formerly known as G Suite.
If your site has a Google Workspace account to give your users unified access to Google apps such as Google Docs, Drive, Calendar, and your company’s GMail-managed email system, then you can configure SSO in Starburst Galaxy to use the same Google login credentials to log into Galaxy.
Google Workspace’s authentication does not support SCIM, so you must manage user accounts in Galaxy.
Configure SAML #
Follow the steps on this page.
-
Go to admin.google.com and log into the admin console with administrator rights for your Google Workspace account.
-
From the menu menu, select Apps > Web and mobile apps.
-
Click Add app and select Add custom SAML app.
-
On the App details page, fill in a name for this app that your users will recognize; the obvious name is
Starburst Galaxy. Optionally fill in a description and upload an image to serve as this app’s icon. If you don’t upload an icon, one is created using the first two letters of the app name.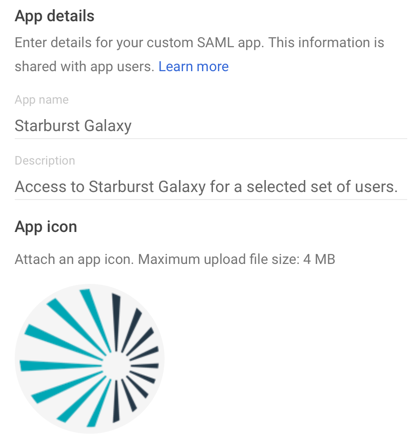
-
When done, click Continue. The resulting pane shows information that Starburst Galaxy needs.
Note: Leave this browser window open to this pane while you open a new browser window. -
In the second browser window, log into Starburst Galaxy with an account granted
accountadminprivileges.
Copy SAML values to Galaxy #
-
In Starburst Galaxy’s navigation menu, open Access > Single sign-on.
-
Click
Configure single sign-on.
If Starburst Galaxy is already configured with an SSO provider, you must delete it before you add a new one. However, first see Delete an SSO provider to understand the consequences of SSO deletion.
-
Select Google Workspace from the Select identity provider options.

-
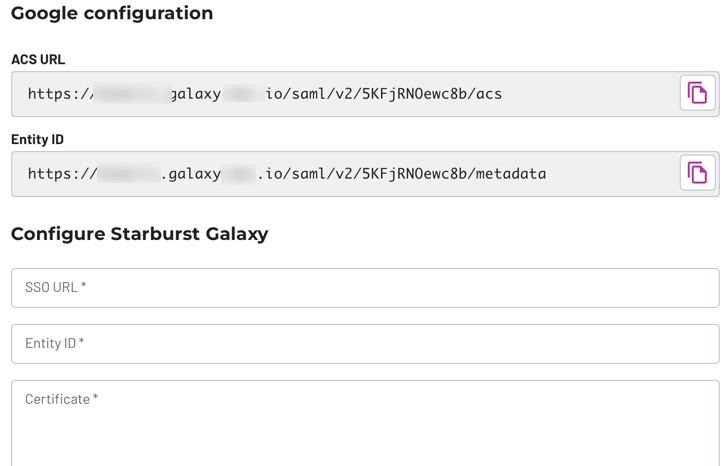
In the Configure Starburst Galaxy section, notice that the three fields have the same label names as the field labels in Option 2 of the Google Admin console you have open in another window.
-
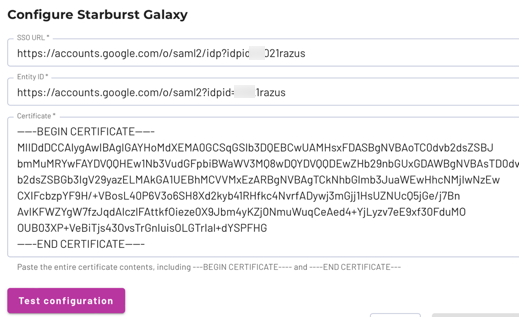
Copy the field values one at a time from the Google Admin console to the matching fields in Starburst Galaxy. Use the copy content_copy button to make sure you get every character, especially from the Certificate field.
Copy SAML values to Google #
-
In the Google Admin browser window, you still have Add custom SAML app showing the Option 2 values.
Click Continue.
-
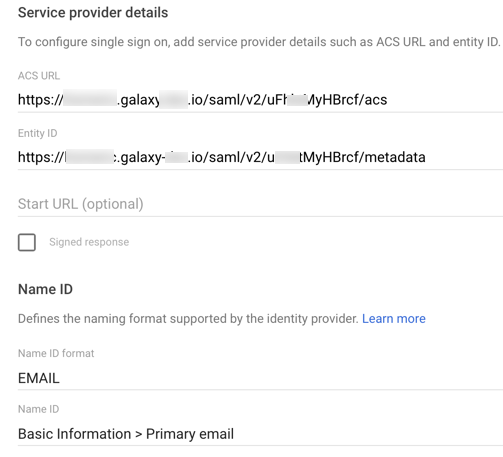
Copy Galaxy’s ACS URL and Entity ID values to the same-named fields in Google Admin.
-
In Google Admin, open the Name ID drop-down, and select
EMAIL. -
Leave the other field values empty or with their default values.
Click Continue.
-
On the next pane, under Google Directory attributes, open the Basic information drop-down and select
Primary email.In the App attributes field, enter
email. -
If necessary, you can return later to this pane later to add further attribute mappings. For now, click Finish.
This generates the SAML app configuration and opens the details page for it.
-
Click OFF for everyone. Change that to ON for everyone and save the change.
-
Click the Service status heading to close this pane.
You can return to this app configuration later to restrict access to a smaller set of usernames.
Test and finish #
-
In Galaxy, click Test configuration. If SAML communication between Google Workspace and Starburst Galaxy is valid, you receive a green success message.
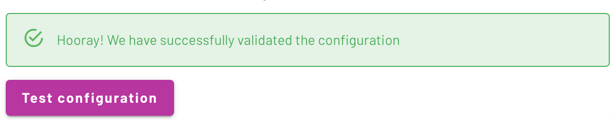
If you receive a red failure message, go back through these steps to make sure there is not a typo or other error.
Configure new user emails #
New users that get added via SCIM can optionally be sent a welcome email. By default this functionality is disabled, but can be enabled by checking the Send welcome email to new users checkbox.

Finish configuration #
With the test confguration successful, click Configure single sign-on to complete the process.

Test Google login #
You can now test logging into Starburst Galaxy with your Google Workspace credentials from the following two directions: from this Admin console, and a normal Starburst Galaxy login.
-
First, open Starburst Galaxy with your non-Google name and password, which are still valid. This ID must have
accountadminrights. -
From the navigation menu, open Access > Users. Add any login names from your Google Workspace membership to which you want to grant access to Starburst Galaxy. Use the full email address for those users as known to Google Workspace, and grant them appropriate role membership.
This step is necessary until Google Workspace supports SCIM and can push usernames down to Starburst Galaxy.
-
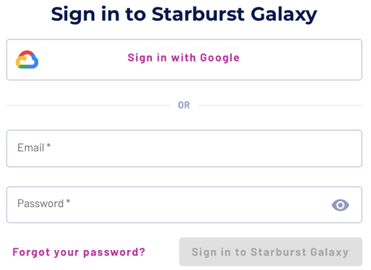
Log out of Starburst Galaxy in order to log back in. The login page has a new Sign in with Google option.
-
Click Sign in with Google, which opens the Google list of accounts if you have more than one. Select a login name that is registered as a Galaxy username. Google prompts you to log into the browser, then opens Galaxy.
If you are already logged in to the current browser session, Google opens Galaxy without further prompts.
The list of Google accounts might be bypassed in these cases:
-
If your current browser session is already logged in with a Google username that is also already a Starburst Galaxy username, then Galaxy opens directly without further prompts.
-
If you have only one Google login name, and it is both logged into the browser and registered as a Galaxy username, then Galaxy opens directly without further prompts.
-
Is the information on this page helpful?
Yes
No