AWS external security #
You must configure sufficient permissions to allow Starburst Galaxy to access your data sources in AWS. The details depend on the connected data source.
The following sections detail the different methods, and explain the necessary steps to configure security and permissions in AWS. You can then use the provided details in your catalog configuration in Starburst Galaxy.
Cross account IAM role #
You can use an AWS cross account IAM role to configure access to data in your catalogs. You can create one role for all catalogs or create multiple roles, as desired.
Use the following steps to create the role or roles with suitable permissions in your AWS console:
-
Access the IAM service configuration from the Security, Identity, & Compliance section of the list of all services.
-
Select Roles from the Identity and Access management menu.
-
Click on the Create role button.
-
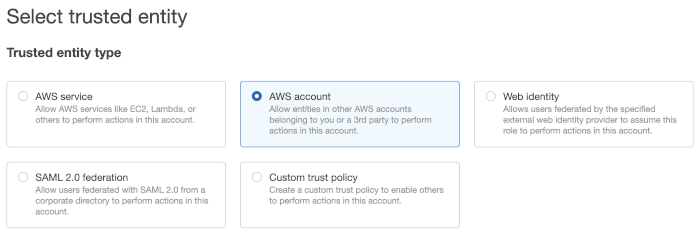
Select AWS account in the Select trusted entity section.
-
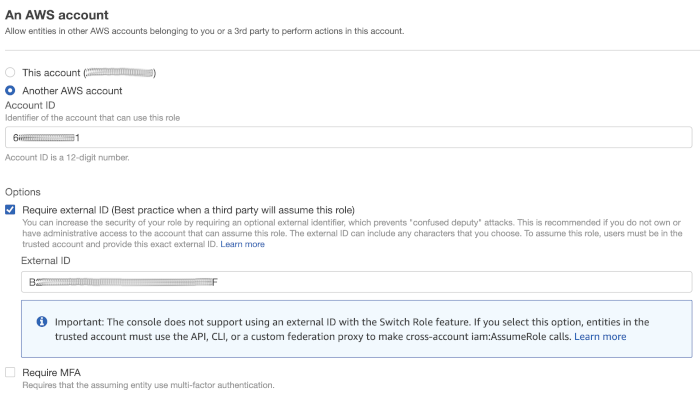
Select Another AWS account in the An AWS account section.
-
In the Starburst Galaxy UI, go to Admin > Cloud settings.
-
On the AWS tab, click Configure IAM role.
-
Copy the Starburst AWS account ID value, and paste it in the Account ID field in the AWS console.
-
In the options section of the dialog, check Require external ID.
-
In the Starburst Galaxy UI, copy the External ID value, and paste it in the External ID field in the AWS console.
-
Click on the Next button.
-
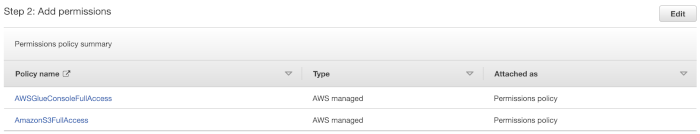
Select the permission policies you would like to attach to the role. To enable access to S3 and AWS Glue, you must select one or more predefined policies from AWS.
-
Click on the Next button.
-
Optionally configure any tags.
-
Click on the Next button.
-
Add a meaningful Role name, such as
starburst-galaxy-access, and provide details in the Description. -
Review permissions in the Permissions policy summary section.
-
Click on the Create role button to finish.
Once the role is created, you can access the necessary details or update the role as desired:
- Use the Search filter to locate the role by name.
- Click on the role name in the list of roles.
-
Copy the value of the ARN from the Summary section to provide the value in Starburst Galaxy. The ARN value looks similar to
arn:aws:iam::youraccountid:role/starburst-galaxy-access.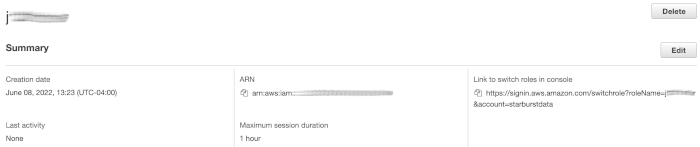
Now you can use the ARN value to configure the authentication for your data source.
AWS access and secret key #
You can use AWS access and secret keys to configure access to data in your catalogs.
Use the following steps to create a user with the necessary access:
-
Access the IAM service configuration from the Security, Identity, & Compliance section of the list of all services.
-
Select Users from the Access management menu.
-
Click Create user.
-
Provide a User name.
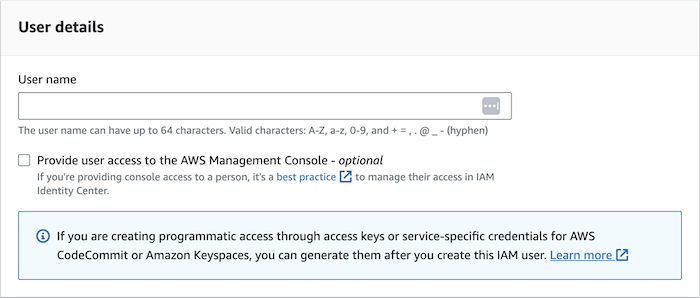
-
Click Next.
-
In Set permissions, select Attach policies directly.
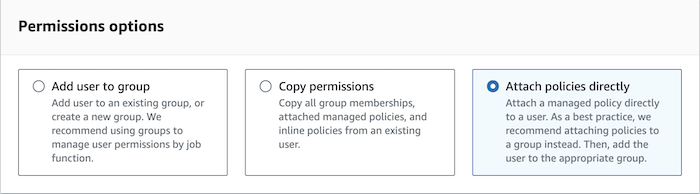
-
Select the Permission policies you would like to attach to the role. To enable access to S3 and AWS Glue, you must select one or more predefined policies from AWS.
-
Click Next.
-
Optionally configure any tags.
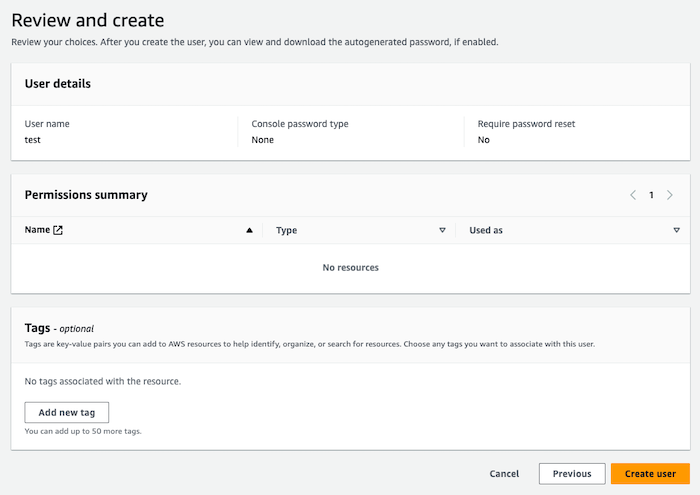
-
Review and click Create user.
The success page provides the Access key ID directly on screen and allows you to access the Secret access key with the Show link. You need to make sure to copy both values for your use. The secret access key value is only available at this stage.
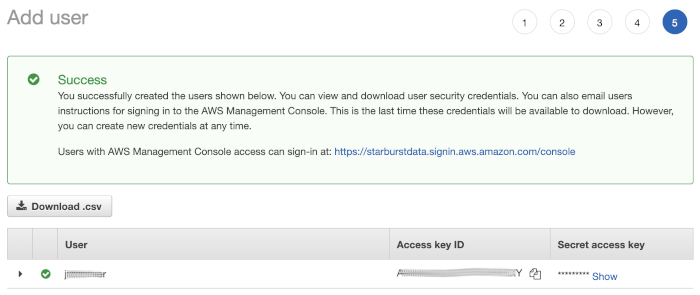
If you do not have the secret access key for the user, you need to use Create new access key in the Security credentials tab of the user Summary.
Now you can use the access key and secret key to configure the authentication for your catalogs.
AWS privileges #
AWS provides a variety of services that require different levels of privileges to be configured to properly manage access and security. The following sections provide details on creating privileges for S3 and Redshift.
S3 privileges #
You need S3 access to get to the files in your buckets. If you are using AWS Glue for the metadata, you also need access to AWS Glue. The level of access varies depending on whether you require read-only or write access to data.
The simplest approach is to use predefined policies from AWS. Depending on your use case, you can use the following policies:
- AmazonS3ReadOnlyAccess: if the role or user is aimed for read access to S3 only.
- AmazonS3FullAccess: if the role or user is aimed for read and write access to S3.
- AWSGlueConsoleFullAccess: if the role or user is aimed to provide access to AWS Glue.
You can set up minimal privileges rather than use some of the more permissive policies provided by AWS.
The following shows a custom privilege example for read-only access to S3:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "s3ReadOnly",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::example-bucket",
"arn:aws:s3:::example-bucket/*"
]
},
{
"Sid": "s3list",
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets"
],
"Resource": [
"*"
]
}
]
}
The following shows a custom privilege example for read/write access to S3:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "s3ReadWrite",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:PutObject",
"s3:DeleteObject",
"s3:AbortMultipartUpload"
],
"Resource": [
"arn:aws:s3:::example-bucket/*",
"arn:aws:s3:::example-bucket"
]
},
{
"Sid": "s3ListBuckets",
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
The following shows a custom privilege example for read/write access to AWS Glue:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "glueReadWrite",
"Effect": "Allow",
"Action": [
"glue:GetDatabases",
"glue:GetDatabase",
"glue:CreateDatabase",
"glue:UpdateDatabase",
"glue:DeleteDatabase",
"glue:GetTables",
"glue:GetTable",
"glue:CreateTable",
"glue:UpdateTable",
"glue:DeleteTable",
"glue:GetPartitions",
"glue:GetPartition",
"glue:CreatePartition",
"glue:UpdatePartition",
"glue:DeletePartition",
"glue:BatchGetPartition",
"glue:BatchCreatePartition",
"glue:BatchUpdatePartition",
"glue:BatchDeletePartition",
"glue:GetColumnStatisticsForTable",
"glue:UpdateColumnStatisticsForTable",
"glue:DeleteColumnStatisticsForTable",
"glue:GetColumnStatisticsForPartition",
"glue:UpdateColumnStatisticsForPartition",
"glue:DeleteColumnStatisticsForPartition"
],
"Resource": "*"
}
]
}
Redshift privileges #
The following shows a custom privilege example for access to Amazon Redshift.
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "redshift:GetClusterCredentials",
"Resource": "arn:aws:redshift:${aws-region}:${aws-account-id}:dbuser:${redshift-cluster-name}/${redshift-username}"
}
}
The
${redshift-username}specified in the policy must exist and match the Redshift username used to configure Starburst Galaxy.
Is the information on this page helpful?
Yes
No