Service accounts #
Service accounts are Starburst Galaxy user accounts assigned for private use by non-human processes such as servers, databases, or automation scripts. Service accounts are typically assigned roles and privileges that are restricted to the smallest set of privileges needed for the account’s purpose.
Use service accounts to restrict access when a non-human process is running. Do not use the account of an actual person for this purpose.
Service account list #
Open the Access control > Service accounts pane to see a list of current service accounts. If none are created yet for this Starburst Galaxy account, this pane shows a Create new service account button.
The list of service accounts has the following columns:
- Service account user name: the login name assigned to this service account.
- Service account domains: the login name combined with this Starburst Galaxy account’s URL.
- Assigned role: the default Galaxy role assigned to this service account to restrict its access privileges.
- Additional roles: any additional Galaxy roles assigned to this service account.
- Created: the date and time this service account was created.
- Password status: a count of the passwords assigned to this service account, if any.
The Search field allows you to search for characters in the user name or domains fields to reduce the service account list to matching lines.
Required privilege #
Your current role must have the Manage service account privilege to allow creating and editing service accounts.
Create a service account #
Before you create a new service account, determine the Galaxy role to assign as default role to the new account. Either edit the privileges of an existing role or create a new role with a set of privileges restricted enough to allow the service account to perform its intended function only.
For example, you might create a service account for a script that logs in to Galaxy, connects to a particular data source, runs a backup function on one table, and writes the backup result file to an Amazon S3 location. This service account only needs Select from table rights for the target table and write access for the S3 location.
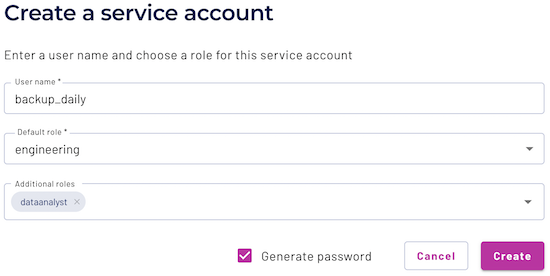
When the role is determined, click the Create new service account button.
- Enter a user name for this service account, using the character set allowed for email names.
- From the drop-down list of default roles, select the role you created or edited to use as default role for this service account.
- From the drop-down list of additional roles, select any additional roles for use by this service account.
-
Select the Generate password checkbox to create the first password for this service account as described in the next section. Clear the checkbox to create the password later.
Edit a service account #
Change the roles for an existing service account by clicking its name in the service account list. Use the drop-down lists to select a different default role or to add or remove additional roles.
You cannot edit a service account’s password, but you can revoke a password and replace it with a new one, as described in the next section.
Service account passwords #
Use Galaxy to generate a secure password. You can do this while creating the service account, described in the previous section, or afterwards.
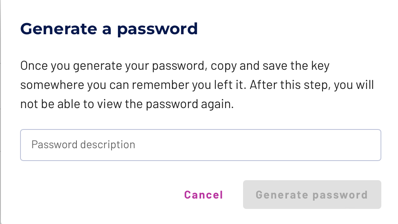
To generate a password for an existing service account, click its name in the service account list to open the Passwords pane. Then click the Generate password link.
In the first dialog, enter a descriptive phrase for this password, then click the Generate password button.
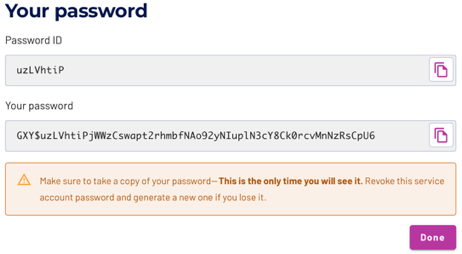
The next dialog shows the generated password. A note in this dialog reminds you that this is the only time you can see the password. Copy the password to a safe place, and use the saved password when setting up login access from this service account to Galaxy.
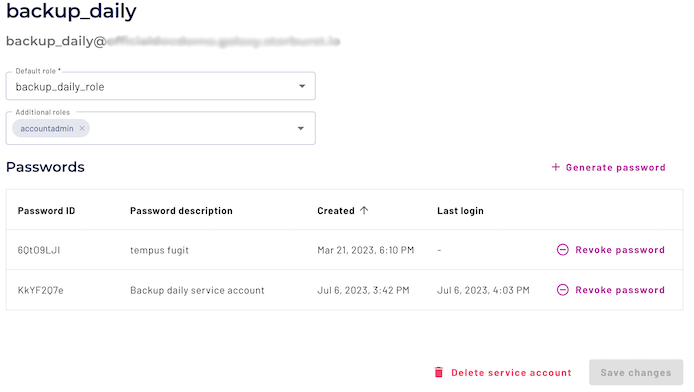
The new password ID then appears in the Passwords list along with the Password description entered in the first dialog, the timestamp of password creation, the timestamp of the last login using the password, and a Revoke password link to disable and remove the current password.
Multiple passwords #
One service account can have more than one password. For example, the account can have a primary password for everyday use, and a one-time password that you give to an administrator for troubleshooting and testing without disclosing the primary password. You can revoke the one-time password after the administrator is done.
In the Passwords list for a service account, click the Generate password link to create subsequent passwords. Keep careful records of the generated passwords.
Use the Revoke password link to disable and remove temporary or obsolete passwords.
Delete a service account #
Delete an existing service account by clicking the more_vert> options menu for the service account in the service account list and selecting Delete service account.
You can also use the Delete service account link at the bottom of the Passwords pane for a service account.
In either case, click Yes, delete in the confirmation dialog to delete the selected service account.
On deletion of a service account, any procedure that was configured to use the deleted service account now fails to authenticate with Starburst Galaxy. You must reconfigure the procedure to use a different service account.
Is the information on this page helpful?
Yes
No