Vulnerability scans #
Automated code scanning tools play an important role in identifying potential security vulnerabilities. When using a code scanner, false positives are a common challenge. False positives occur when a code scanner incorrectly identifies a security vulnerability that does not pose a genuine risk.
The page explains why false positives occur in code scans, the limitations of automated code scanning tools, and Starburst’s procedure for handling and addressing false positives.
Causes of false positives #
Understanding the reasons for false positives in security scans is important for effectively managing and addressing them. False positives may occur for the following reasons:
- Complex code environments: Starburst deployments are complex. Their extensive codebases contain intricate logic, frameworks, and libraries, making them susceptible to misinterpretations by code scanning tools.
- Limitations of automated scanners: Code scanners rely on predefined rules, patterns, and algorithms to identify vulnerabilities. While these rules are valuable for detecting common issues, they are not infallible. If a code snippet exhibits a pattern that aligns with a scanner’s predefined rules, the scanner may indicate a vulnerability, even when there is not a genuine security threat.
- Lack of context: Code scanners lack access to the SEP
source code, so they lack understanding of the broader context in which your
code operates. Because code scanners analyze code components in isolation from
one another, they do not consider how these code components interact within
the broader context of the entire environment. The narrow scope of code
scanning
tools leads to misinterpretations of code, resulting in false positives.
- Starburst relies on Veracode as our source of CVE truth. Our ability to upload our codebase to Veracode gives us confidence in providing accurate reports on potential security vulnerabilities.
- Frequent code changes: In software development environments, frequent updates are the norm. Because code scanners may not be aware of the latest code modifications made by Starburst Engineering, they may falsely flag code segments as security vulnerabilities.
- Lack of human analysis: The human analysis of code plays an essential role
in differentiating between false positives and genuine security risks.
Security experts and software developers can review code to discern whether a
reported issue is a legitimate issue. Even when using the latest code scanning
tools, human intervention is necessary.
- Starburst Engineering reviews code scanning reports as a standard practice. We provide the security teams of top organizations with thorough explanations and detailed understandings of their findings.
Handling false positives #
False positives have significant implications for broader security assessment processes. For this reason, it is important to manage them effectively.
Starburst’s standard procedure for handling false positives is designed to maintain the accuracy of security assessments. This procedure includes the following steps:
- Conduct a code scan: If it is required for your compliance, conduct a code scan on the SEP product.
- Highlight findings: In the event of any critical findings in your code scan, send your results to Starburst Engineering for further analysis.
- Identify false positives: Starburst Engineering reviews your findings and identifies any false positives.
- Mark CVEs: Starburst Engineering marks each CVE as either “not exploitable,” “approved,” or “no application impact.” These markings ensure that the CVEs are not flagged on future code scanning reports.
Case study #
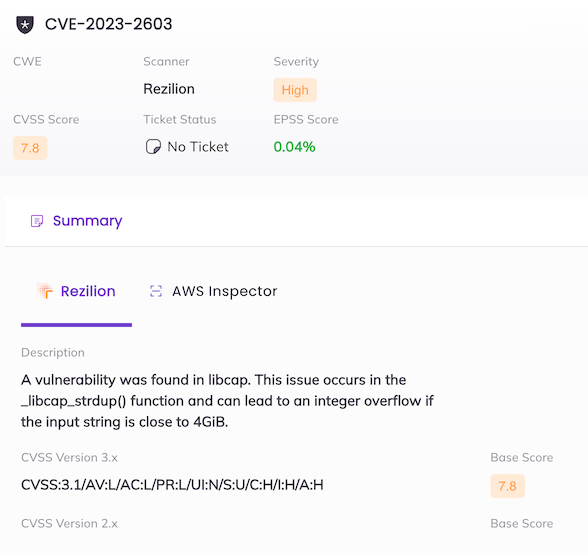
This section describes a case study that illustrates Starburst Engineering’s handling of false positives. Specifically, the study outlines a scenario involving CVE-2023-2603, a vulnerability that appears frequently in customer scans. The description for this CVE reads as follows:
A vulnerability was found in libcap. This issue occurs in the _libcap_strdup()
function and can lead to an integer overflow if the input string is close to
4GiB.
Vulnerability analysis and review #
First, Starburst Engineering reviewed the flagged finding. When evaluating CVE 2023-2603 in Rezilion, we identified the library associated with this CVE within our codebase. However, we determined that this library is not exploitable, nor is it used by our product.
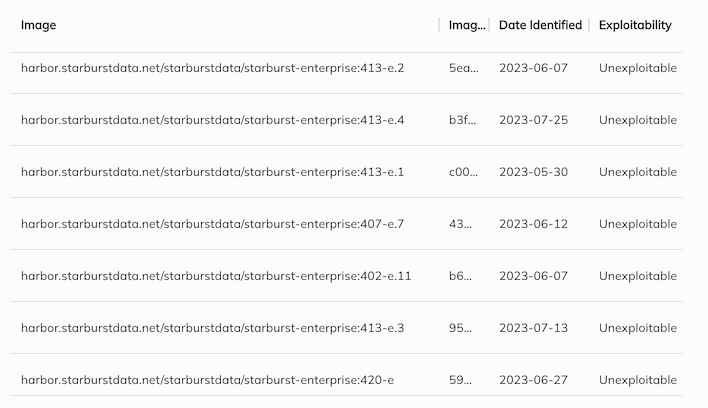
False positive confirmation #
Starburst Enterprise’s product composition consists of open-source JARs due to backward compatibility requirements. While those JARs are included in our codebase, SEP’s reliance on them is minimal. Crucially, SEP relies on components of the JARs are not connected to the libraries responsible for the CVE.
Risk mitigation #
To mitigate potential security risks, Starburst Engineering ensured that the SEP code does not interact with the libraries associated with this CVE. Though it is possible to perform upgrades of JAR versions, Starburst is committed to backward compatibility requirements. Adherence to those requirements necessitates that we use components of the JAR files that are not related to the libraries responsible for the CVE.
Solution #
Starburst Engineering confirmed that CVE 2023-2603 was a false positive. The CVE was marked with a “not exploitable” designation in the code scanning tool to prevent the recurrence of this false positive in future code scans.
Starburst Engineering took all necessary steps to ensure that SEP’s code does not interact with the specifically vulnerable libraries that have caused CVE 2023-2603.
Additional resources #
- Per Red
Hat,
“Scan results with a greater number of findings can be tempting to be
viewed as more accurate than scans with less; however, that’s not always the
case. A truly accurate scan will remove duplicates, utilize vendor-disclosed
data, and assist the security professional in prioritizing the elimination of
risk.”
- Code scanning tools get their value from producing an output of as many flagged items as possible. This is attractive from a sales perspective, since it allows a code scanner to show value to buyers.
- Per Microsoft,
“Pentests from scanners frequently produce false positives which do not
constitute a security risk. Often pentest reported issues are related to
software not being patched with the most current update. In addition, many
issues are configuration related rather than a software vulnerability. It is a
best practice to manually verify the issue reported.”
- You can do this by contacting Starburst to review your code scan report.
Is the information on this page helpful?
Yes
No